Tactical Urbanism: Short-term Action for Long-term Change : Lydon, Mike, Garcia, Anthony, Duany, Andres: Amazon.es: Libros
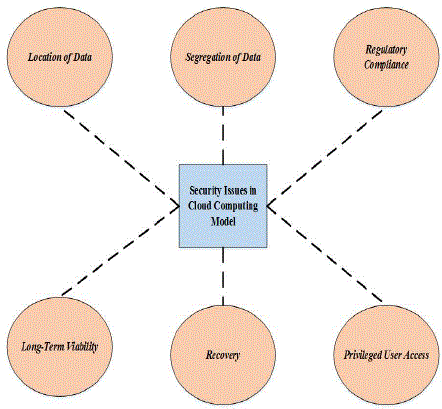
A Study on Key Integrity and Data Security Verification For Cloud Computing Environment - Ignited Minds Journals

Cloud Computing Adoption Theoritical Model 4. DISCUSION The intention... | Download Scientific Diagram
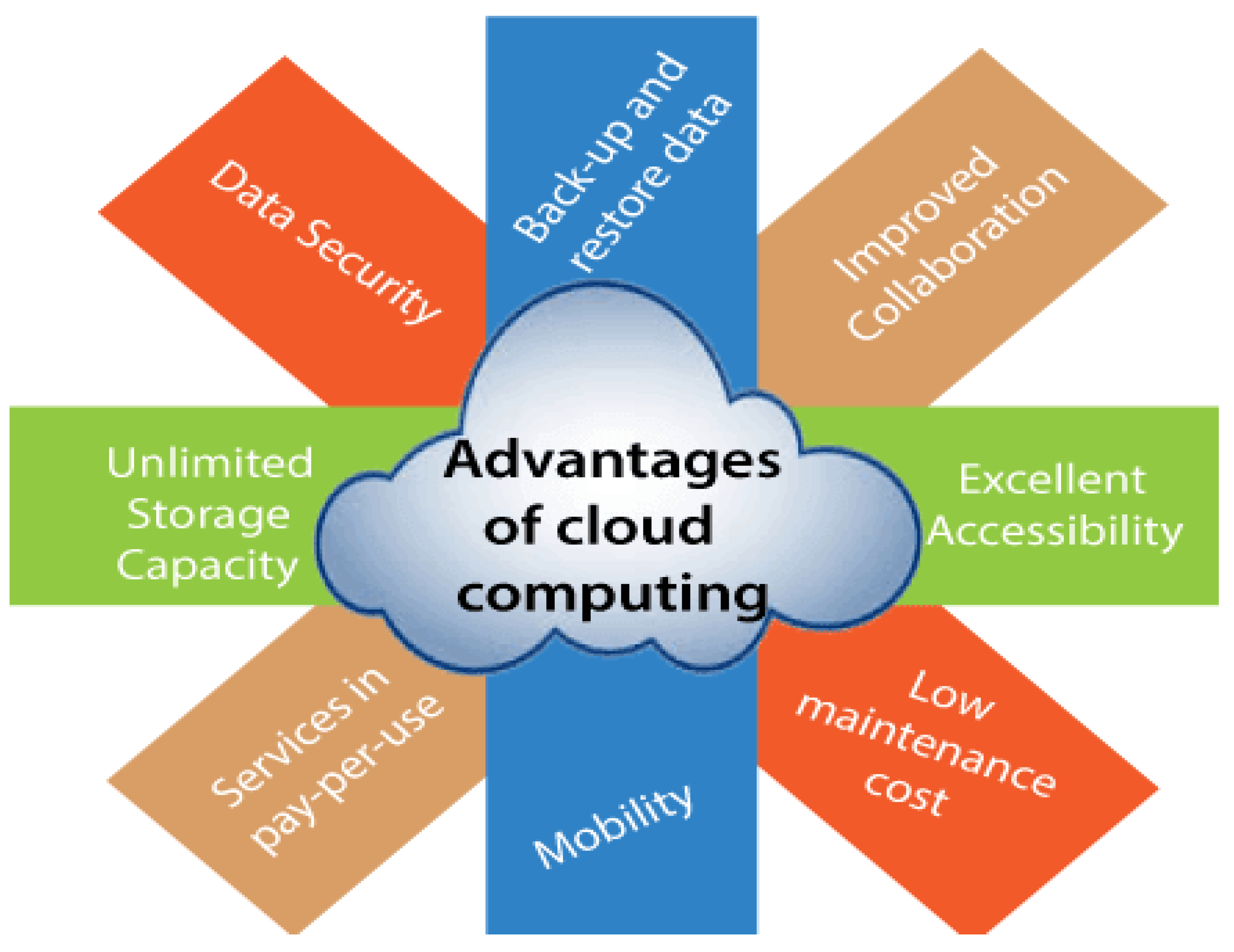
Sustainability | Free Full-Text | Probing Determinants Affecting Intention to Adopt Cloud Technology in E-Government Systems

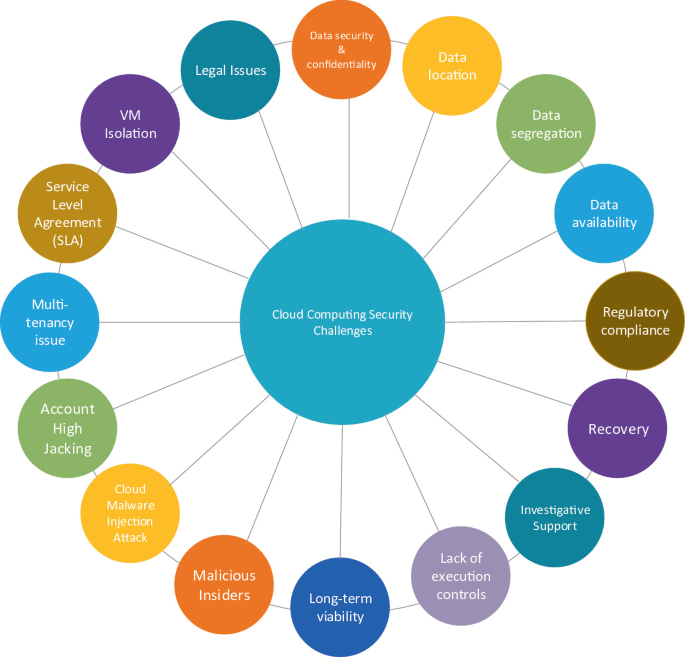
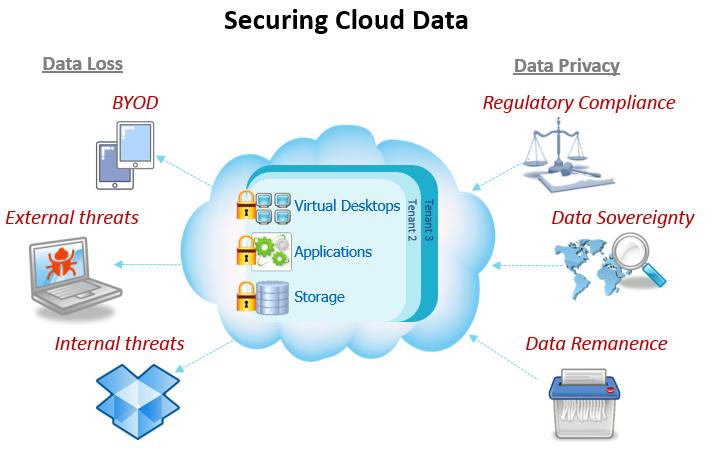
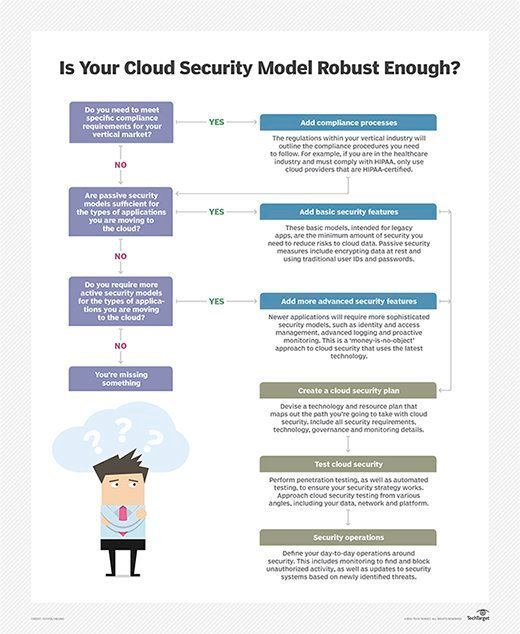
Cloud Computing Issues. Why Is "Security" Everywhere on That Slide? Security is generally perceived as a huge issue for the cloud: During a keynote. - ppt download
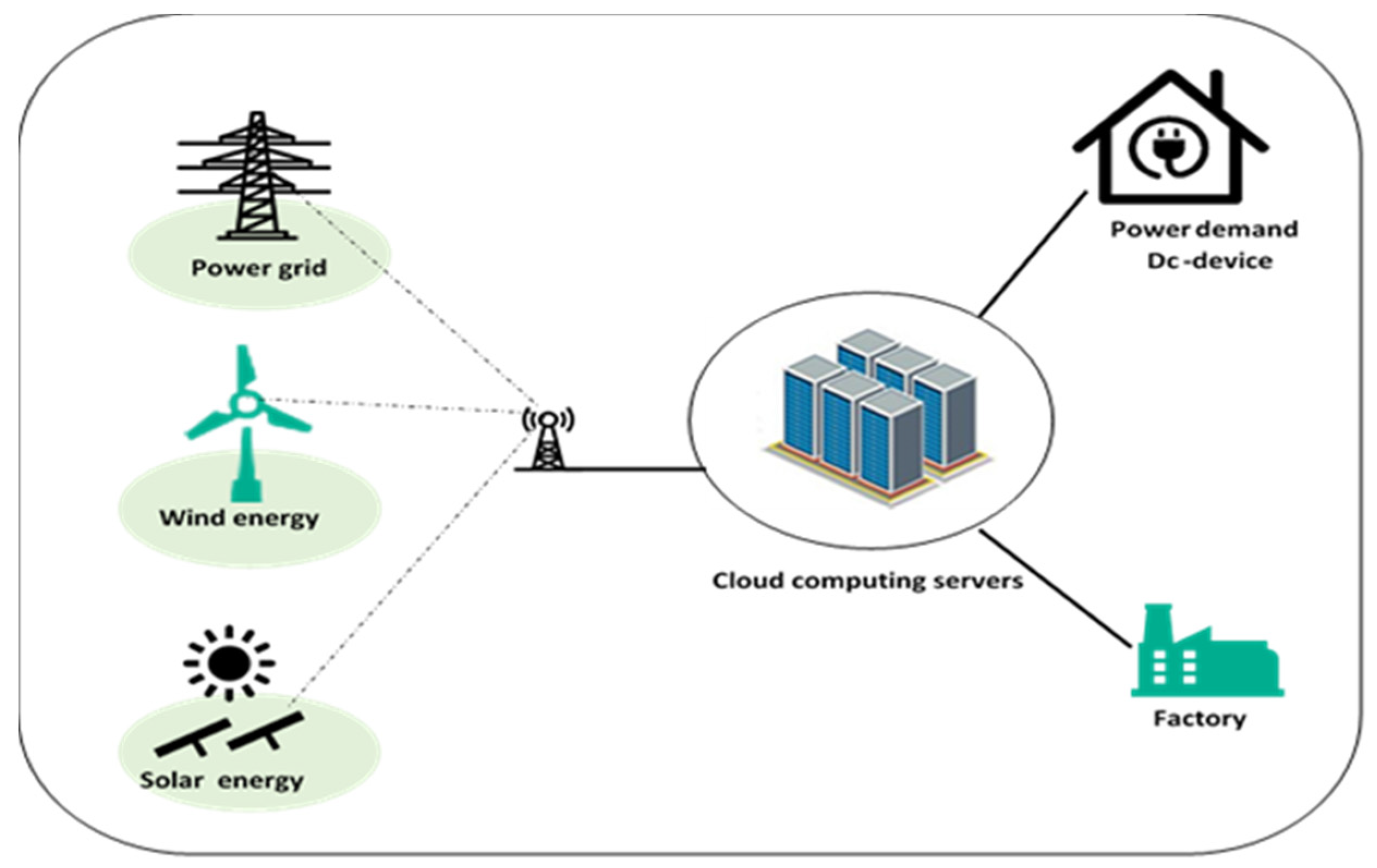
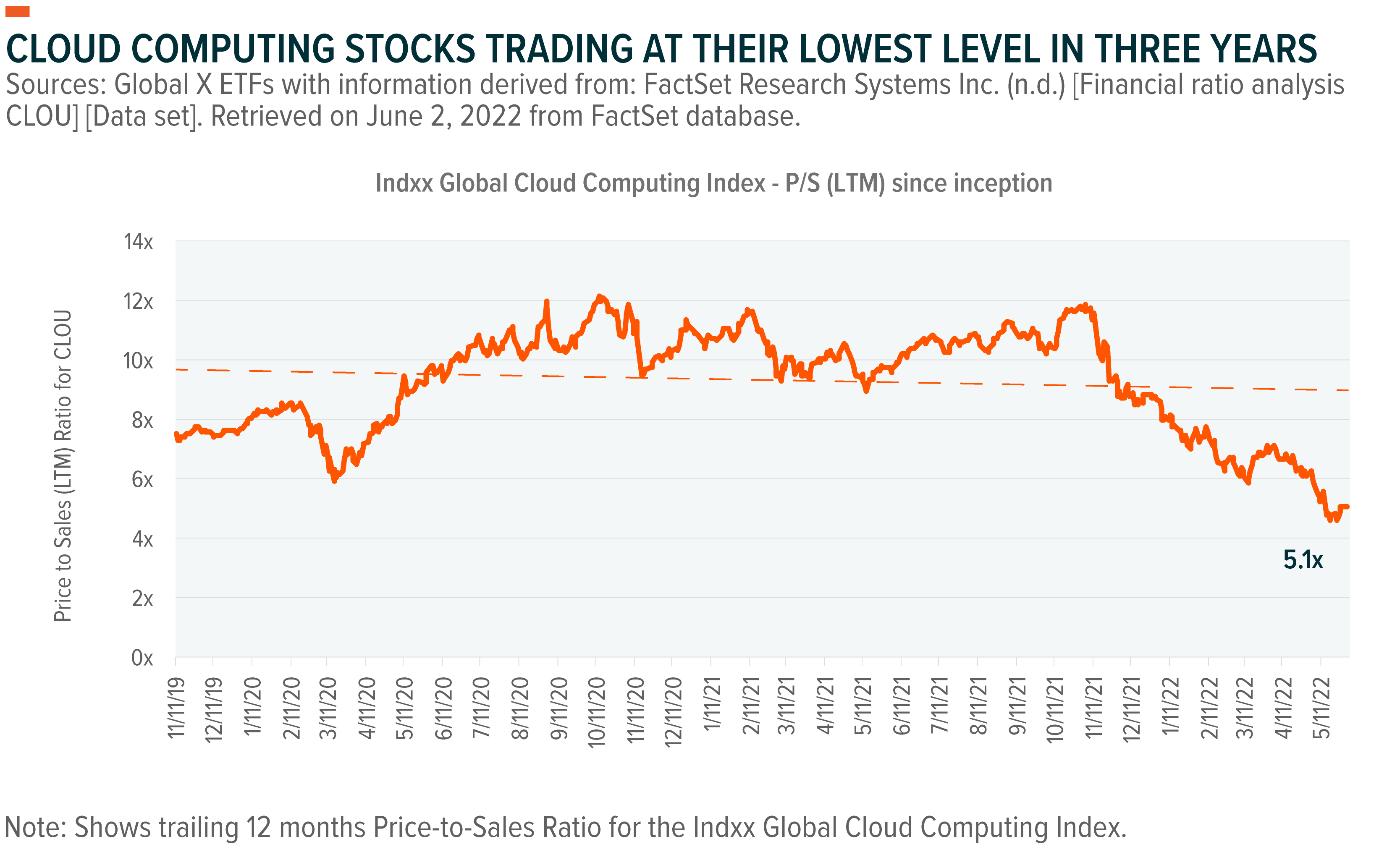
Applied Sciences | Free Full-Text | A Conceptual and Systematics for Intelligent Power Management System-Based Cloud Computing: Prospects, and Challenges